In a digital world filled with evolving cyber threats, safeguarding your online accounts is crucial. Two-Factor Authentication (2FA) provides an extra layer of security to protect your personal information. This guide will walk you through the process of setting up 2FA on your accounts, significantly reducing the risk of unauthorized access.
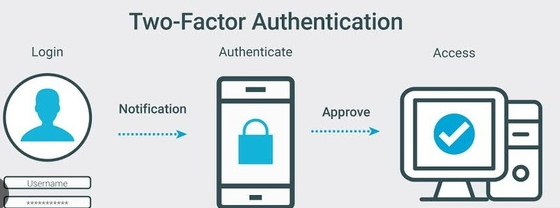
Table of Contents
- What Is Two-Factor Authentication (2FA)?
- Why You Need 2FA
- Common 2FA Methods
- Step-by-Step Guide to Set Up 2FA
- Tips for Using 2FA Effectively
- Two-Factor Authentication Best Practices
- Final Thoughts
1. What Is Two-Factor Authentication (2FA)?
Two-Factor Authentication, often abbreviated as 2FA, is an extra layer of security that requires not only a password and username but also something that only the user has on them. This additional layer ensures that even if someone discovers your password, they won’t be able to access your account without the second authentication method.
2. Why You Need 2FA
- Enhanced Security: 2FA adds a critical layer of protection against unauthorized access.
- Password Vulnerabilities: Passwords can be stolen or guessed, leaving your accounts at risk.
- Data Privacy: 2FA helps safeguard your personal information, emails, financial data, and more.
- Compliance: Many regulatory requirements mandate the use of 2FA for certain industries.
3. Common 2FA Methods
There are several common 2FA methods:
- Text Message (SMS) Codes: You receive a code on your mobile device via SMS.
- Authentication Apps: Apps like Google Authenticator, Authy, or Microsoft Authenticator generate time-based codes.
- Email Codes: You receive a code via email.
- Biometrics: Fingerprint or facial recognition is used as the second factor.
- Hardware Tokens: Physical devices generate codes.
- Backup Codes: Pre-generated codes for use when other methods are unavailable.
4. Step-by-Step Guide to Set Up 2FA
Step 1: Choose the Platform
Select an online platform or service that supports 2FA. Common platforms include Google, Facebook, Twitter, and financial institutions.
Step 2: Access Security Settings
Log in to your account and navigate to the account or security settings. Look for an option related to 2FA or Multi-Factor Authentication (MFA).
Step 3: Enable 2FA
Enable 2FA for your account. This typically involves turning it on and selecting your preferred method, such as SMS, app, or email.
Step 4: Follow the Setup Process
For SMS or email-based 2FA, you’ll receive a code during setup. For authentication apps, you’ll need to scan a QR code provided by the service. If you’re using hardware tokens, follow the manufacturer’s instructions.
Step 5: Verify the Setup
Once you’ve entered the code or confirmed the setup, your 2FA method is active. You may need to verify it with a test code.
Step 6: Generate Backup Codes
Most platforms allow you to generate backup codes. Keep these codes in a secure location in case your primary 2FA method is unavailable.
Step 7: Test Your 2FA
Log out of your account and attempt to log back in. You’ll need to enter the 2FA code or use your selected method.
5. Tips for Using 2FA Effectively
- Keep your 2FA method secure and confidential.
- Use a backup method in case your primary 2FA method fails.
- Update your recovery phone or email if you change contact information.
6. Two-Factor Authentication Best Practices
- Use 2FA for your email accounts, which often serve as recovery options for other services.
- Enable 2FA for financial and sensitive accounts.
- Regularly review and update your 2FA methods and backup codes.
- Stay informed about 2FA best practices and new authentication methods.
7. Final Thoughts
Setting up Two-Factor Authentication is a proactive step in securing your online presence. It’s a simple yet highly effective way to protect your accounts and sensitive information from unauthorized access. With 2FA in place, you can confidently navigate the digital world while keeping your personal data safe.
